Program
Program at a Glance
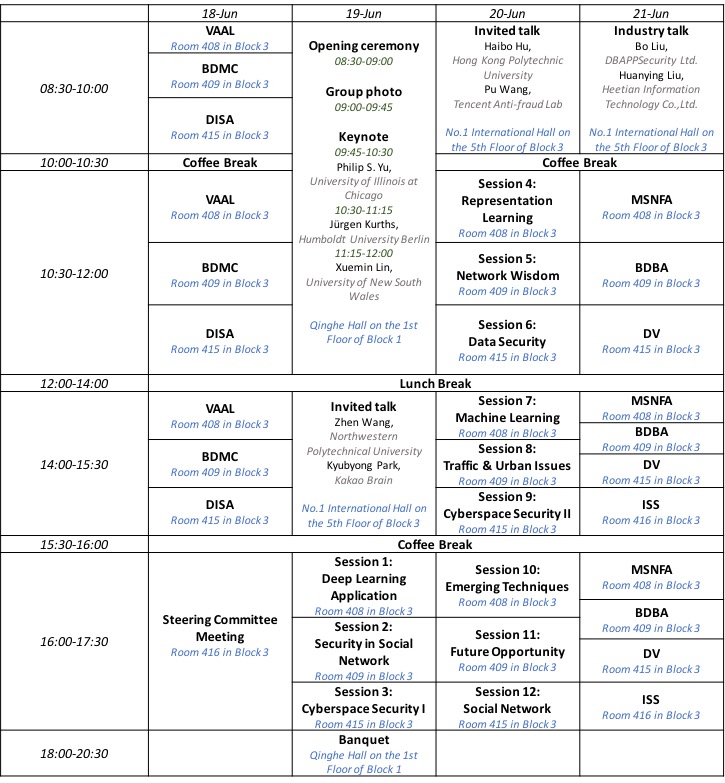
Main Technical Program
Session 1: Deep Learning Application
Session Chair: Guopeng Zhou, Peking University First HospitalJune 19th, 16:00-17:30, Room 408 in Block 3
-
The Real Time Gait Phase Detection Based On Long Short-Term Memory
Zhen Ding, Chifu Yang (Harbin Institude of Technology), Kai Xing, Xueyan Ma, Kai Yang (Nanjing General Hospital of Nanjing Military Command), Hao Guo, Chunzhi Yi (Harbin Institute of Technology) and Feng Jiang (Nanjing General Hospital of Nanjing Military Command) -
Neural Network Based Clinical Treatment Decision Support System for Co-existing Medical Conditions
Yichun Duan (Peking University), Guopeng Zhou (Peking University First Hospital), Yuanxing Zhang, Zhaoqian Lan (Peking University), Chunhua Chi (Peking University First Hospital) and Wei Yan (Peking University) -
AI-assisted Prediction on Potential Health Risks with Regular Physical Examination Records
Zhaoqian Lan (Peking University), Guopeng Zhou (Peking University First Hospital), Yichun Duan and Wei Yan (Peking University) -
Multi-Level Composite Neural Networks for Medical Question Answer Matching
Dong Ye, Sheng Zhang, Hui Wang, Jiajun Cheng, Xin Zhang, Zhaoyun Ding and Pei Li (National University of Defense Technology) -
Question Classification Based on MAC-LSTM
Bengong Yu, Qingtang Xu and Peihang Zhang (Hefei University of Technology)
Session 2: Security in Social Network
Session Chair: Chen-Yi Lin, National Taichung University Of Science And TechnologyJune 19th, 16:00-17:30, Room 409 in Block 3
-
Efficiently Preserving Privacy on Large Trajectory Datasets
Chen-Yi Lin, Yuan-Chen Wang, Wan-Tian Fu, Yun-Sheng Chen, Kuan-Chen Chien and Bing-Yi Lin (National Taichung University Of Science And Technology) -
Evolutionary Game Based Analysis for User Privacy Protection Behaviors in Social Networks
Fang Liu, Li Pan and Li-hong Yao (Shanghai Jiaotong University, China) -
Privacy-aware Personal Information Propagation Management in Social Networks
Yu Wu and Li Pan (Shanghai Jiaotong University, China) -
Toward Predicting Communication Effectiveness
Zeshan Peng, Wenbo Wang, Yi Shang, Bitty Balducci and Detelina Marinova (University of Missouri) -
Early Detection of Rumors in Heterogeneous Mobile Social Network
Yuanxing Zhang, Kaigui Bian (Peking University), Lin Chen (Yale University), Shaoling Dong (Fibonacci Data Consulting Services Inc.), Lingyang Song and Xiaoming Li (Peking University)
Session 3: Cyberspace security I
Session Chair: Gaoxiang Zhang, Peking UniversityJune 19th, 16:00-17:30, Room 415 in Block 3
-
A Position-based Secure Fast Handover Mechanism for High-speed Trains
Yue Zhao, Zhouguo Chen (Science and Technology on Communication Security Laboratory), Hong Su, Enbo Sun, Yubin Guo (The Thirtieth Research Institute of China Electronic Technology Group Corporation) and Jianwei Ding (Science and Technology on Communication Security Laboratory) -
Generic Generating Functions for the Counting Functions of Quadratic Functions With Prescribed Walsh Spectrum
Xiaolong Yang, Mengce Zheng and Honggang Hu (University of Science and Technology of China) -
SLBot: A Serverless Botnet Based on Service Flux
Di Wu (Institute of Information Engineering,Chinese Academy of Sciences), Binxing Fang (Beijing University of Posts and Telecommunications), Jie Yin, Fangjiao Zhang, and Xiang Cui (Institute of Information Engineering, CAS, China) -
JMS: Joint Bandwidth Allocation and Flow Assignment for Transfers with Multiple Sources
Geng Li (Yale University), Yichen Qian (Tongji University), Lili Liu (Tsinghua University) and Y.Richard Yang (Yale University) -
RansomTracer: Exploiting Cyber Deception for Ransomware Tracing
Zihan Wang, Xu Wu (Beijing University of Posts and Telecommunications), Chaoge Liu, Qixu Liu (Institute of Information Engineering, Chinese Academy of Sciences, China) and Jialai Zhang (Sichuan University)
Session 4: Representation Learning
Session Chair: Chaoyang Li, Tsinghua UniversityJune 20th, 10:30-12:00, Room 408 in Block 3
-
Fast Top-k Area Topics Extraction with Knowledge Base
Fang Zhang, Xiaochen Wang (Tsinghua University), Jingfei Han (Beihang University), Jie Tang and Shiyin Wang (Tsinghua University) -
User Tagging in MOOCs through Network Embedding
Chaoyang Li, Zhengyang Song and Jie Tang (Tsinghua University) -
Course Concept Extraction in MOOC via Explicit/Implicit Representation
Xiaochen Wang, Wenzheng Feng, Jie Tang and Qingyang Zhong (Tsinghua University) -
Topic Analysis Model for Online Social Network
Yan Jia, Lu Deng, Bin Zhou (National University of Defense Technology), Binxing Fang (Beijing University of Posts and Telecommunications), Weihong Han (Guangzhou University), Aiping Li, Qiang Liu and Yong Quan (National University of Defense Technology) -
ULE: Learning User and Location Embeddings for POI Recommendation
Hao Wang, Wentao Ouyang, Huawei Shen and Xueqi Cheng (Institute of Computing Technology, CAS, China)
Session 5: Network Wisdom
Session Chair: Zhaoquan Gu, Guangzhou UniversityJune 20th, 10:30-12:00, Room 409 in Block 3
-
Approximation Algorithms for Controller Placement Problems in Software Defined Networks
Tianshu Li, Zhaoquan Gu (Guangzhou University), Xiao Lin (Tsinghua University), Shudong Li and Qingfeng Tan (GuangZhou University) -
How to Control Target Nodes in Dynamic Networks
Zhaoquan Gu (Guangzhou University), Yongcai Wang (Renming University), Jing Qiu, Lihua Yin and Zhihong Tian (Guangzhou University) -
Reasoning about Cloud Storage Systems
Hanpin Wang, Zhao Jin, Lei Zhang, Yuxin Jing, Jiang Xu and Yongzhi Cao (Peking University) -
Bitcoin Mixing Detection Using Deep Autoencoder
Lihao Nan and Dacheng Tao (University of Sydney) -
A Data Storage Method Based on Blockchain for Decentralization DNS
Jingqiang Liu (Institute of Information Engineering, Chinese Academy of Sciences, China), Bin Li, Lizhang Chen, Meng Hou, Feiran Xiang and Peijun Wang (Harbin Institute of Technology)
Session 6: Data security
Session Chair: Yuguang Xu, Peking UniversityJune 20th, 10:30-12:00, Room 415 in Block 3
-
Identity-Based Blind Proxy Re-Signature Scheme for Data Security
Xiaodong Yang, Likun Xiao, Yutong Li (Northwest Normal University), Shudong Li (Guangzhou University), Jinli Wang and Chunlin Chen (Northwest Normal University) -
Robust Audio Watermarking Algorithm Based on Air Channel Characteristics
Wen Diao, Yuanxin Wu, Weiming Zhang, Bin Liu and Nenghai Yu (University of Science and Technology of China) -
H-Securebox: A Hardened Memory Data Protection Framework on ARM Devices
Zhangkai Zhang, Zhoujun Li, Chunhe Xia (Beihang University), Jinhua Cui (Singapore Management University) and Jinxin Ma (China Information Technology Security Evaluation Center) -
Study on Security Technology of Internet of Things Based on Network Coding
Yejun Zhou, Lede Qiu, Hang Yu (Institute of Telecommunication Satellite, CAST) and Chunhui Sun (Shanghai Fire Research Institute of MPS) -
Complete Graph Random Number Generator and Symmetrical Design Scheme
Yuguang Xu, Hanpin Wang and Hongyu Wang (Peking University)
Session 7: Machine Learning
Session Chair: Mingyuan Ma, Peking UniversityJune 20th, 14:00-15:30, Room 408 in Block 3
-
Lip Segmentation with Muti-Scale Features Based on Fully Convolution Network
Zhen Ju, Xiang Lin, Fangqi Li and Shilin Wang (Shanghai Jiaotong University) -
Performance Comparison of Deep Learning Techniques for Recognizing Birds in Aerial Images
Yang Liu, Peng Sun, Max R. Highsmith, Nickolas M. Wergeles (University of Missouri), Joel Sartwell and Andy Raedeke (Missouri Department of Conservation), Mary Mitchell, Heath Hagy (U.S. Fish and Wildlife Service), Andrew D. Gilbert (University of Illinois), Brian Lubinski (U.S. Fish and Wildlife Service) and Yi Shang (University of Missouri) -
Image Encryption Algorithm Based on Memristive BAM Neural Networks
Jiuhong Xiao, Weiping Wang and Meiqi Wang (University of Science and Technology Beijing) -
Stochastic Alternating Direction Method of Multipliers with Conjugate Gradient
Mingyuan Ma and Dongyang Zhao (Peking University) -
Evaluating the Rationality of Judicial Decision with LSTM-based Case Modeling
Shang Li, Hongli Zhang, Lin Ye, Xiaoding Guo and Binxing Fang (Harbin Institute of Technology)
Session 8: Traffic & Urban issues
Session Chair: Khouanetheva Pholsena, Shanghai Jiaotong UniversityJune 20th, 14:00-15:30, Room 409 in Block 3
-
Deep CNN-based Methods to Evaluate Neighborhood-Scale Urban Valuation through Street Scenes Perception
Junhan Zhao, Xiang Liu, Yanqun Kuang, Yingjie Victor Chen and Baijian Yang (Purdue University) -
Research of Urban Land Use and Regional Functions Based on Mobile Data Traffic
Qing Miao, Yuanyuan Qiao and Jie Yang (Beijing University of Posts and Telecommunications) -
A Robust Change-point Detection Method by Eliminating Sparse Noises from Time Series
Kun Qin, Lei Sun (Beijing Institute of Technology), Bo Liu, Yuan Fan (DBAPPSecurity Ltd) and Kar-Ann Toh (Yonsei University) -
Urban Road Congestion Condition Discrimination Research Based on Vector Features
Zhiming Ding, Fujie Ren, Zhi Cai and Yang Cao (Beijing University of Technology) -
Traffic Status Evaluation Based on Possibilistic Fuzzy C-Means Clustering Algorithm
Khouanetheva Pholsena and Li Pan (Shanghai Jiaotong University, China)
Session 9: Cyberspace security II
Session Chair: Xiaoyun Li, Beijing University of Posts and Telecommunications; Chaoge Liu, Institute of Information Engineering Chinese Academy of SciencesJune 20th, 14:00-15:30, Room 415 in Block 3
-
Micro-Honeypot: Using Browser Fingerprinting To Track Attackers
Zhaopeng Jia (Beijing University of Posts and Telecommunications), Xiang Cui (Guangzhou University), Qixu Liu, Xiaoxi Wang and Chaoge Liu (Institute of Information Engineering Chinese Academy of Sciences) -
Constructing Browser Fingerprint Tracking Chain Based on LSTM Model
Xiaoyun Li (Beijing University of Posts and Telecommunications), Xiang Cui (Guangzhou University), Limin Shi (Shandong University of Science and Technology), Chaoge Liu and Xiaoxi Wang (Institute of Information Engineering Chinese Academy of Sciences) -
MaliceScript: A Novel Browser-based Intranet Threat
Chaoge Liu (Institute of Information Engineering Chinese Academy of Sciences), Xiang Cui (Guangzhou University), Zhi Wang, Xiaoxi Wang, Yun Feng (Institute of Information Engineering Chinese Academy of Sciences) and Xiaoyun Li (Beijing University of Posts and Telecommunications) -
Webshell Detection Based on Random Forest--Gradient Boosting Decision Tree Algorithm
Handong Cui, Delu Huang, Yong Fang, Liang Liu and Cheng Huang (Sichuan University) -
Automatically Crawling Dynamic Web Applications via Proxy-based JavaScript Injection and Runtime Analysis
Yan Li, Peiyi Han (Beijing University of Posts and Telecommunications), Chuanyi Liu and Binxing Fang (Harbin Institute of Technology (Shenzhen))
Session 10: Emerging techniques
Session Chair: Yifan Zhang, Peking UniversityJune 20th, 16:00-17:30, Room 408 in Block 3
-
SAQP++: Bridging the Gap between Sampling-based Approximate Query Processing and Aggregate Precomputation
Dongxiang Zhang (National University of Defense Technology), Mingtao Lei (Beijing University of Posts and Telecommunications) and Xiang Zhu (National University of Defense Technology) -
Research on Vulnerability of Space Information Network Based on Interdependent Networks
Zhongwen Zhao, Zhangyuan Li (Space Engineering University), Huanghuang Guo (63710 Troops) and Miaoben Yang (Space Engineering University) -
Structural Vulnerability of Complex Networks Under Multiple Edge-Based Attacks
Xiaobo Wu (Yantai Vocational College), Shudong Li (Guangzhou University), Aiping Li, Bin Zhou (National University of Defense Technology) Zhihong Tian (Guangzhou University) and Dawei Zhao (Shandong Computer Science Center) -
Structural Brain Network Mining based on Core Theory
Yifan Zhang, Kan Zhang (Peking University) and Xinyi Zou (Harbin Institute of Technology)
Session 11: Future opportunity
Session Chair: Jiayin Qi, Beijing University of Posts and TelecommunicationsJune 20th, 16:00-17:30, Room 409 in Block 3
-
The Research about Public Sentiment Differences between the Belt and Road Countries on China's Hot Issues
Fulian Yin, Yiming Ma, Congcong Zhang and Jinbao Song (Communication University of China) -
Research on Discrete Emotion Classification of Chinese Online Product Reviews Based on OCC Model
Lina Liu and Jiayin Qi (Beijing University of Posts and Telecommunications) -
TigerAware: An Innovative Mobile Survey and Sensor Data Collection and Analytics System
William Morrison, Luke Guerdan, Jayanth Kanugo, Yi Shang and Timothy Trull (University of Missouri) -
The Coming Era of AlphaHacking?
Tiantian Ji, Yue Wu, Chang Wang, Xi Zhang and Zhongru Wang (Beijing University of Posts and Telecommunications)
Session 12: Social Network
Session Chair: Xiaomeng Wang, Harbin Institute of TechnologyJune 20th, 16:00-17:30, Room 415 in Block 3
-
The Social Negative Mood Index for Social Networks
Rui Jin, Hongli Zhang and Yu Zhang (Harbin Institute of Technology) -
Virtual Community Detection Model and Related Research in Online Social Networks
Yan Jia, Qiang Liu (National University of Defense Technology), Binxing Fang (Beijing University of Posts and Telecommunications), Bin Zhou, Lu Deng and Yong Quan (National University of Defense Technology) -
Predicting the popularity of online content based on the weak ties theory
Xiaomeng Wang, Binxing Fang, Hongli Zhang (Harbin Institute of Technology), and Shen Su (Guangzhou University) -
A Practical Approach to Answer Extraction for Constructing QA Solution
Mingxuan Xiong (The First High School of Changsha), Aiping Li, Zongsheng Xie and Yan Jia(National University of Defense Technology)
Workshops
Big Data and Business Analytics (BDBA 2018)
June 21th, 10:30-12:00, 14:00-15:30, 16:00-17:30, Room 409 in Block 3- Will the Big Data Strategic Alliance Be Workable for Intelligent Vehicles and New Energy Vehicles Industry?—Perspective of System Dynamics
- Distributed Large Scale Privacy-Preserving Deep Mining
- Transfer Pretrained Sentence Encoder to Sentiment Classification
- Application of Improved Grey Model GM(1,1) in Prediction of Human Health Data
- Hybrid Recommendation Algorithm Based on Social Interaction and Tag Weight
- Ownership Concentration, Internal Control Quality and Real Earnings Management
- Dockless Bike-sharing Reallocation based on Data Analysis: Solving Complex Problem with Simple Method
- Sentiment Analysis Based on Deep Learning and its Application in Screening for Perinatal Depression
- Design and Implementation of Information Dissemination Simulation Algorithm in Large-Scale Complex Network Based on Spark
- A Bayesian Personalized Ranking Algorithm Based on Tag Preference
- Customized Bundle Recommendation by Association Rules of Product Categories for Online Supermarkets
Big Data Mining for Cyberspace (BDMC 2018)
June 18th, 08:30-10:00, Room 409 in Block 3- Insider Threat Detection Using Characterizing User Behavior
- An Intelligent Network Attack Detection Method Based on RNN
- A Novel Approach for Detecting Browser-based Silent Miner
- A Metadata-Based Representation Method of The Internet of Things
- Authentication of Multiple-User Spatial Keywords Queries
June 18th, 10:30-12:00, Room 409 in Block 3
- Automated Fuzz Generators for High-Coverage Tests Based on Program Branch Predications
- Mode Decomposition Based Hybrid Model for Traffic Flow Prediction
- A Method Based on Statistical Characteristics for Detection Malware Requests in Network Traffic
- An Improved Uniform Identity Authentication Method Based on SAML in Cloud Environment
- A Location Privacy-aware Method for kNN Query in Location Based Services
June 18th, 14:00-15:30, Room 409 in Block 3
- Hand Gesture Recognition Based On Deep Learning Method
- A Novel Automatic Diagnosis Based Physical Therapy For Duchenne Muscular Dystrophy Children
- Video Frame Interpolation Based on Multi-Scale Convolutional Network and Adversarial Training
- Analysis on the Influence Factors of the Medical Institutions' Medical Efficiency Change in China
Data Intelligence and Security Analysis (DISA 2018)
June 18th, 08:30-10:00, 10:30-12:00, 14:00-15:30, Room 415 in Block 3- Efficient Identity-Based Offline/Online Encryption Scheme for Lightweight Devices
- Deep Learning based Attribute Classification Insider Threat Detection for Data Security
- Ensemble Steganography
- An In-depth Study of Digits in Passwords for Chinese Websites
- Chaotic-map Image Encryption Scheme based on AES Key Producing Schedule
- Automatic Generation of Review Content in Specific Domain of Social Network Based on RNN
- A Novel Blockchain-Based Authenticated Key Exchange Protocol and Its Applications
- Advanced Slide Attacks on the Even-Mansour Scheme
- Learning Automata based Feature Selection for Network Traffic Intrusion Detection
- Anomaly Detection for Power Grid Flow Patterns Based on the multi-Restricted Boltzmann Machines
- A Content Auditing Method of IPsec VPN
- Web Service applying Moving Target Defense
- A Passive-measurement-guided Tree Network Surveying and Mapping Model
- A Survey on Collaborative Deep Learning and Privacy-Preserving
- Detection of Malicious Domain Names Based on Hidden Markov Model
- Decentralized Privacy Preserving Reputation System
Data Visualization (DV 2018)
June 21th, 10:30-12:00, 14:00-15:30, 16:00-17:30, Room 415 in Block 3- Research on the Prediction Method of Power Battery SOC Based on Deep Learning
- The Feature Representation Ability of Variational AutoEncoder
- Multimodal Object Classification using Bidirectional Gated Recurrent Unit Networks
- Sparse Weighted Naive Bayes Classifier for Efficient Classification of Categorical Data
- A Categorically Reweighted Feature Extraction Method for Anomaly Detection
- A Joint Decoding Algorithm for Named Entity Recognition
- Establishment of Computer-Aided Diagnosis System for Liver Tumor CT Based on SVM
- A Tensor-Based Sub-Mode Coordinate Algorithm for Stock Prediction
- Detecting Pyramid Scheme Accounts with Time Series Financial Transactions
- Visualization of Pairwise Data: an Overview
- Hyperspectral Image Denoising base on Adaptive Sparse Representation
- Tactical Wireless Network Visualization: Requirements and Representations
- Reasearch on Dynamic Evolution Model Visualization of Satellite Communication Network Based on Complex Network
- A Speedup Spatial Rearrangement Algorithm for Dynamic Network Visualization
- Generation Framework for Situation Visualization Service from The Perspective of Cognition
- A Multi-layer Network Topology Visualization Layout Based on Louvain Community Detection
- Research on the Technology of Electromagnetic Information Modeling and Visual Analysis
- Convolutional Neural Networks Based for High Spectral Dimensional Data Classification
Intelligent System Security (ISS 2018)
June 21th, 14:00-15:30, 16:00-17:30, Room 416 in Block 3- A PCA-based Model to Predict Adversarial Examples on Q-Learning of Path Finding
- Adversarial Examples Construction towards White-Box Q Table Variation in DQN Pathfinding Training
- Intention-aware Multi-channel Keyword Extension for Content Security
- A RF-PSO Based Hybrid Feature Selection Model in Intrusion Detection System
- An Approach to Generate Topic Similar Document by Seed Extraction-based SeqGAN Training for Bait Document
Multi-Source Network Fusion and Analysis (MSNFA 2018)
June 21th, 10:30-12:00, 14:00-15:30, 16:00-17:30, Room 408 in Block 3- Evaluation on Availability of Entity Information in Cyberspace
- Prediction Of Twist Angle For Assistive Exoskeleton Based On EMG Signals
- A Matrix-Based Apriori Algorithm Improvement
- A Hierarchical Demand Prediction Method with Station Clustering for Bike Sharing System
- Automatic Taxonomy Construction for Eye Colors Data without Using Context Information
- A Pricing Model for Self-Help Investigation Offline Based on Multivariate Linear Regression Analysis
- Research on Improve Topic Representation over Short Text
- Realistic Traffic Data based Mobility Modeling and Simulation of Smart EV
- An Approach for Evaluating User Participation in Bitcoin
- Representation Learning Based on Influence of Node for Multiplex Network
- Exploiting Structured News Information to Improve Event Detection via Dual-level Clustering
- Expert Identification based on dynamic LDA topic model
Vulnerability Analysis and Adversarial Learning (VAAL 2018)
June 18th, 08:30-10:00, 10:30-12:00, 14:00-15:30, Room 408 in Block 3- De-anonymizing Social Networks User via Profile Similarity
- BlockCAM: A Blockchain-based Cross-domain Authentication Model
- A Method of Fast Locating the Key Nodes Based on the Distribution Law of Node's Propagation Domain
- A Survey on Security of Cloud Environment: Threats, Solutions, and Innovation
- OFC: An Approach for Protecting Location Privacy from Location Provider in Location-Based Services
- Remote Protocol Vulnerability Discovery for Intelligent Transportation Systems (ITS)
- Data-Driven Vulnerability Pattern Analysis for Fuzzing
- Research on Security of Key Algorithms in Intelligent Driving System
- A Vulnerability Test Method for Speech Recognition Systems Based on Frequency Signal Processing
- Who are in the Darknet? Measurement and Analysis of Darknet Person Attributes
- Analysis on the related Evaluation Technique of Composite Attack in Network Confrontation









